Over the years, I’ve had the opportunity to test a wide variety of document review platforms. Some, like Relativity and OmniX, seem to do a great job of solving certain review challenges, particularly in large projects. Some, which I won’t name, can be frustrating no matter the type and size of project. Others focus on solving specific challenges and are great options for specific needs. One of those recurring challenges is clearly small project eDiscovery.
Many of the larger, more complex tools really are best suited for use in an environment that has made a significant investment in technology, tuning and support. On a small case, it can be difficult and impractical to use some platforms. Fortunately, the folks at Logikcull have stepped in to solve this problem with a self-service, fully automated eDiscovery platform.
Occasionally, I have cases I’m personally handling that are far too small to worry with sending through the normal workflow I’d use on a larger case. Usually the eDiscovery needs on these small, generally pro-bono matters, don’t require a complex tool. Creating a PST of the relevant documents and exporting to PDF, then adding on any scanned documents will suffice. Sometimes, however, a case that seems small will suddenly explode, such as when a client explained to me, just a few days before a discovery deadline, that she’d discovered a backup of a PST containing documents we’d not yet reviewed.
I was able to create a PST of the relevant documents quickly, but my normal export to PDF method was far to cumbersome for the specific population, which included numerous attachments I’d need to manually extract. Instead, I decided to look for a simple, self-managed tool to process and create the production and was met with limited success.
The team at Logikcull, however, left a comment and suggested I give their product a try. Having met my deadline through other means, I took a look at their offering (which I previously had heard about only in a gimmicky, “you can review documents on a smart watch” way) and was thoroughly impressed.
 They sent me a link for a free trial and I logged in to create my account. I was immediately able to create a new project, specifying a few options like how to render Word, Powerpoint and Excel files and what sort of deduplication I desired.
They sent me a link for a free trial and I logged in to create my account. I was immediately able to create a new project, specifying a few options like how to render Word, Powerpoint and Excel files and what sort of deduplication I desired.
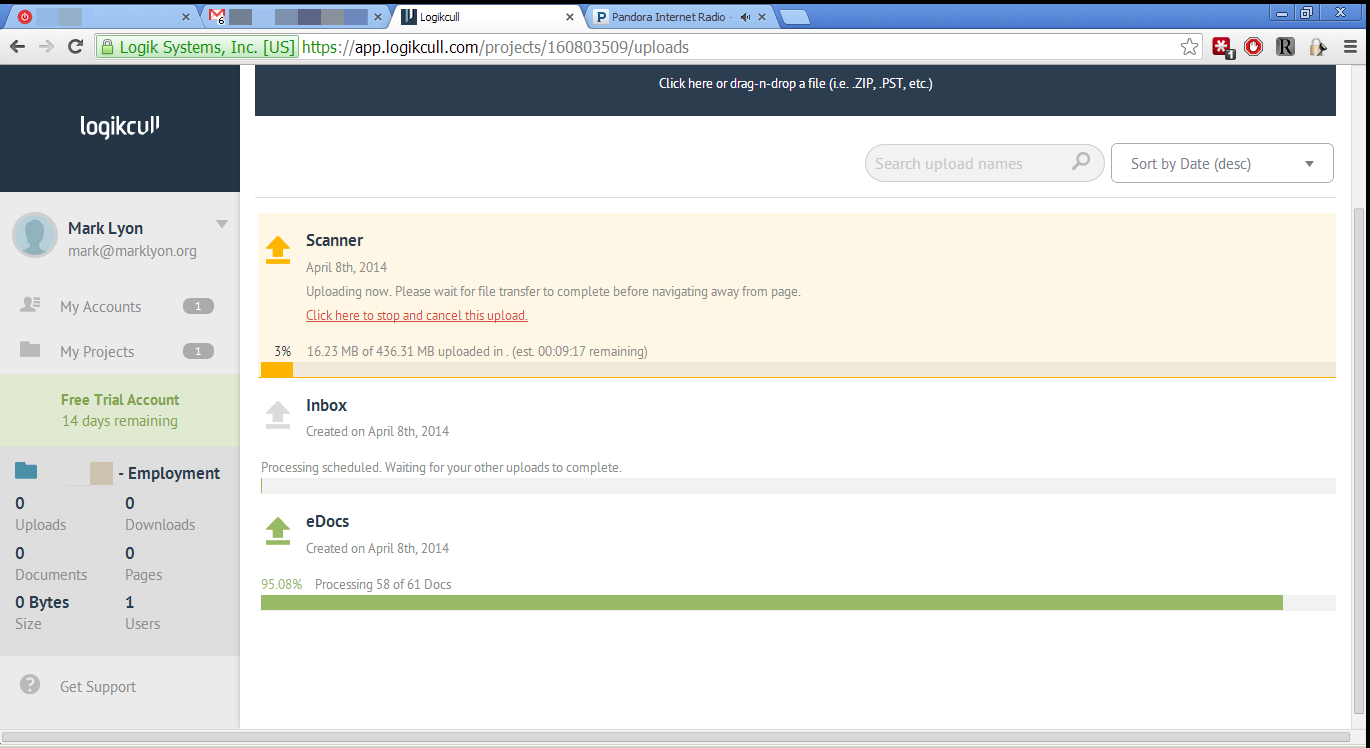
With that accomplished, I was able to immediately start uploading data, using a drag and drop interface, right from their web page. The process could not have been simpler and, when my connection dropped out in the middle of one large file, the system immediately resumed when I clicked “restart”. While one file uploaded, the others started processing; the entire operation was finished in a few minutes while I handled other matters.
 With processing complete, I was given a mini-report that included the number of documents, file size, and even how many exceptions required special handling. The documents were immediately available to me and I was able to start coding right away.
With processing complete, I was given a mini-report that included the number of documents, file size, and even how many exceptions required special handling. The documents were immediately available to me and I was able to start coding right away.
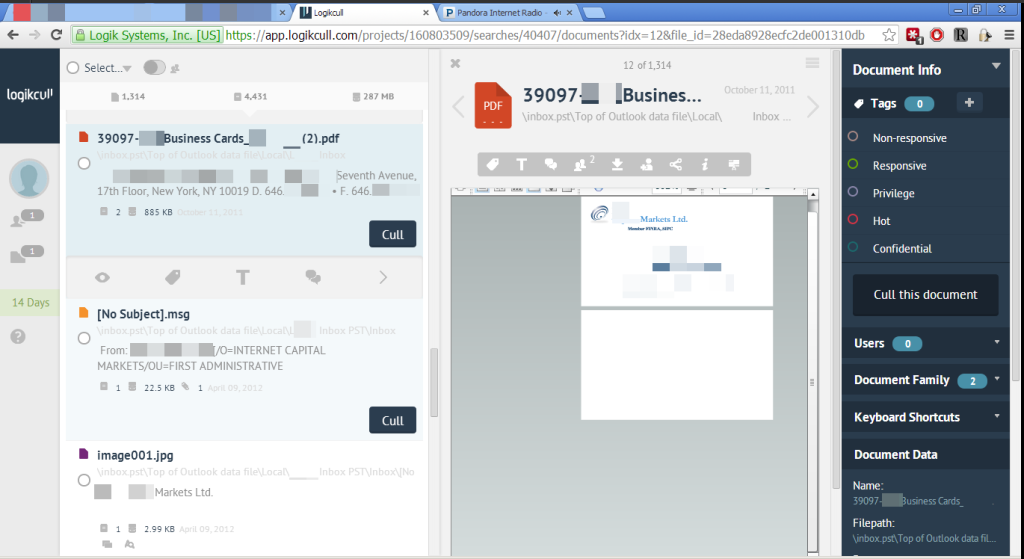
The review interface is geared toward small, focused review teams working on the project. Many options are available as one reviews, but all documents are rendered in a TIFF-like viewer (though, no special plugins or downloads are required – the entire review interface works with standard web browsers like Google Chrome).
Searches were easily built using uploads, custodians, tags or keywords. Once a search is saved, it can then be exported as a production, immediately, right in the web interface. In my discussions with the Logikcull team, they even plan to offer the option to send a secure download link (with delivery notification) to the opposing parties, eliminating even the need to download and re-send the file.
The production tool offers a number of pre-built templates for delivery to Relativity, the DOJ, SEC and FTC. They also allow users to define their own templates as needed. The step-by-step tool then asks a user to specify the load file format, choose image, native file and text file options and to include optional reports. Once the options are set, a name is assigned and a starting bates number given, and the production assembles itself and alerts you when the download is ready.
- Step 1 – Population and Families
- Step 2 – Metadata Template
- Step 3 – Assembly Instructions
- Step 4 – Bates Numbers
- Step 5 – Assembly & Download
The tool would easily accommodate a same-day turnaround of loading and production and is easily handled by just one attorney.
While there are some limitations of the platform designed to impose some uniformity and allow it to operate with little intervention from their support team, users willing to make minor adjustments to their workflow to accommodate its process will easily find that they can self-manage their small projects and produce high-quality results.
Having started in a small law firm, this tool would have been incredibly valuable on numerous cases and the pricing was recently (as of 6/30/14) changed to a per user, per year model that is well within the realm of reasonableness for small firms. Each user costs $2,500 per year (with a sliding scale of discounts for buying longer terms or more seats) and comes with 5gb of upload space per seat (upload space is based on uploaded file size). Additional uploads cost $100/gb (and again, discounts are available if you buy in bulk). There do not appear to be limitations on the number of separate cases that can be configured. For a limited time, users who sign up will receive no recurring cost storage, eliminating any concern over monthly costs for long-running cases. Because their system creates TIFFs and PDFs on ingestion, there are also no costs involved in making productions in either format. The value of the simplicity, speed and flexibility cannot be understated.
If you’re a tech-savvy attorney working on a small project or at a firm without an existing eDiscovery infrastructure, Logikcull is certainly worth testing. You may find that it serves many of your needs quite well.